In this blog i will show how to configure Quality Gates in SonarQube server.
What is Quality Gate?
Quality Gate is combination of various conditions, against which SonarQube server measures project quality thresholds. There are different categories/severity of issue which sonar reports, like Critical, Blocker, Major, Code Coverage, blocker issues since last build and many others.
Before I explain further, let me explain when need arises to create custom quality gates.
Sonarqube works with many technologies, all these technologies will have different standard and process. And measuring criteria can't be same for all these applications, in such scenarios different Quality Gates will be needed for each of these projects/application.
Now moving on with the Quality Gate creation process.
Login to SonarQube server, for me it is hosted at "http://localhost:9000/", incase it defers then access the url on which sonarqube server is hosted.
Login to sonarqube portal, click on Menu "Quality Gates" in top menu bar.
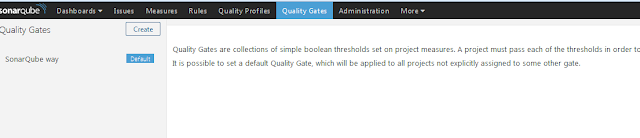
Sonar will show default Quality Gate which comes with Sonar setup.
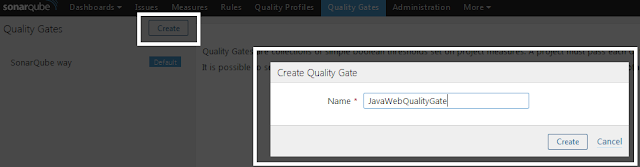
To create new Quality Gate, click on "Create" button in left navigation. Enter quality gate name and click on Create button in the popup.
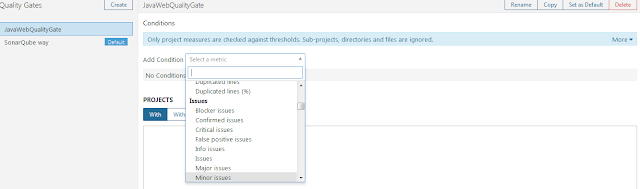
Click on "Add Condition" drop down and select the appropriate metrics specific to project requirement.
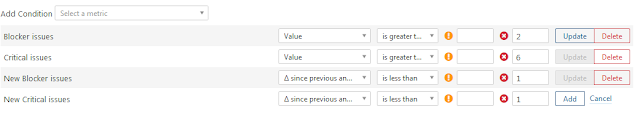
after adding the conditions, select following details for each row.
After above step, project needs to be associated to Quality Gate.
In below project display area on the same screen, search for the project and select the checkbox, which will associate the project to created Quality Gate.
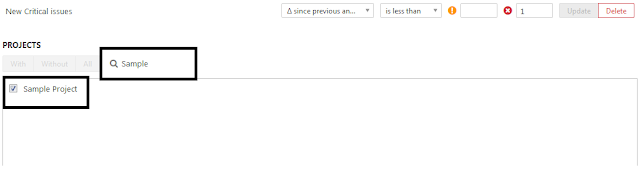
This is last step in creation of Custom Quality Gate.
For the above project if new build is initiated then it will validate the project against this quality gate. That can be verified in logs.
What is Quality Gate?
Quality Gate is combination of various conditions, against which SonarQube server measures project quality thresholds. There are different categories/severity of issue which sonar reports, like Critical, Blocker, Major, Code Coverage, blocker issues since last build and many others.
Before I explain further, let me explain when need arises to create custom quality gates.
Sonarqube works with many technologies, all these technologies will have different standard and process. And measuring criteria can't be same for all these applications, in such scenarios different Quality Gates will be needed for each of these projects/application.
Now moving on with the Quality Gate creation process.
Login to SonarQube server, for me it is hosted at "http://localhost:9000/", incase it defers then access the url on which sonarqube server is hosted.
Login to sonarqube portal, click on Menu "Quality Gates" in top menu bar.

Sonar will show default Quality Gate which comes with Sonar setup.
To create new Quality Gate, click on "Create" button in left navigation. Enter quality gate name and click on Create button in the popup.

Click on "Add Condition" drop down and select the appropriate metrics specific to project requirement.

after adding the conditions, select following details for each row.
- First Drop Down - select the value
- Second Drop Down - select the condition
- Warning Field Value- value
- Error Field Value - enter value
Next will click on "Add" button. It will add the metrics to QualityGate. There are many metrics which is provided in the dropdown, select based on the project needs.

After above step, project needs to be associated to Quality Gate.
In below project display area on the same screen, search for the project and select the checkbox, which will associate the project to created Quality Gate.

This is last step in creation of Custom Quality Gate.
For the above project if new build is initiated then it will validate the project against this quality gate. That can be verified in logs.











